This type of code is used typically in Java to implement what are often recognized as listener objects that contain code to handle consumer interface events. Such objects normally want access to the context in which they're outlined to hold out an appropriate action, so it's handy that Java supplies one thing like a closure. For instance, within the code above, the inner technique couldn't discuss with the native variable x. In Java, you possibly can discuss with native variables provided that they've been declared to be final.I don't wish to take the time to elucidate all of the details of inner lessons. The point is that this is a case the place practical languages like ML have influenced languages like Java. In reality, I witnessed many attention-grabbing discussions about including one thing like closures to C#. In the end, Microsoft determined to add something more highly effective than Java's inner courses. They are called anonymous methods and they permit you to refer to local variables in addition to fields and methods of the outer object, which signifies that it represents a true closure . Per default, objects might be checked before any inserts or updates are made by Hibernate ORM. Pre deletion events will per default not trigger a validation. The values of those properties are the comma-separated fully specified class names of the teams to validate. Example eleven.1, "Manual configuration of BeanValidationEvenListener" exhibits the default values for these properties. The behavior of sophistication or its instances is defined using methods. Methods are subroutines with the power to operate on objects or courses. These operations might alter the state of an object or simply provide ways of accessing it. Many kinds of methods exist, however support for them varies throughout languages. Some forms of strategies are created and known as by programmer code, whereas different special methods—such as constructors, destructors, and conversion operators—are created and called by compiler-generated code. A language can also permit the programmer to define and name these special methods. SEI CERT SEC05-J rule forbids the use of reflection to increase accessibility of classes, strategies or fields. An attacker code might name this method and cross such class to create an instance of it.
This should be averted by both making the method non-public or by checking for bundle access permission on the package deal. A third risk is to make use of the java.beans.Beans.instantiate() methodology as a substitute of java.lang.Class.newInstance() which checks whether or not the Class object being acquired has any public constructors. (Feel free to implement your personal properties utilizing non-public fields internally.) This will just run the get andset strategies defined for the property. In this case, studying the property will always get the worth forty two, and writing it'll simply trigger a message to be printed. The client simply accesses the property, and the thing can handle that nonetheless it sees fit. Static technique objectsStatic method objects provide a way of defeating the transformation of perform objects to technique objects described above. A static method object is a wrapper round some other object, usually a user-defined method object. When a static technique object is retrieved from a category or a category occasion, the object actually returned is the wrapped object, which isn't topic to any additional transformation. Static technique objects are created by the built-in staticmethod() constructor. Note that the transformation from operate object to instance method object happens each time the attribute is retrieved from the instance. In some circumstances, a fruitful optimization is to assign the attribute to a neighborhood variable and name that local variable. Also discover that this transformation only occurs for user-defined functions; different callable objects (and all non-callable objects) are retrieved without transformation. It is also necessary to note that user-defined functions that are attributes of a category instance are not converted to sure strategies; this solely occurs when the perform is an attribute of the category. This class implements the Serializable interface, however does not define a serialVersionUID field. Also, completely different source code to bytecode compilers may use totally different naming conventions for artificial variables generated for references to class objects or inner courses. To guarantee interoperability of Serializable across variations, consider adding an explicit serialVersionUID. Object getSource()Returns the object that fired the event.Note that the getSource method returns an Object. Event courses generally outline strategies similar to getSource, but that have extra restricted return types. For instance, the ComponentEvent class defines a getComponent technique that identical to getSource returns the item that fired the event. The difference is that getComponent at all times returns a Component.
Each how-to page for event listeners mentions whether you must use getSource or one other technique to get the event supply. This part discusses several design concerns to remember when implementing event handlers in your software. We then introduce you to event objects small objects that describe every event. In specific, we speak about EventObject, the superclass for all AWT and Swing events. Next, we introduce the ideas of low-level events and semantic occasions, recommending that you simply choose semantic events when possible. The the rest of this section discusses implementation techniques you may use in some event listeners or see in event listeners created by different folks or by GUI builders. A public methodology of a public class may be known as from exterior the package which implies that untrusted information could additionally be handed to it. Calling a technique before the doPrivileged to examine its return value after which calling the same technique inside the class is dangerous if the tactic or its enclosing class isn't ultimate. For example, a technique returning a file path could return a harmless path to verify before entering the doPrivileged block and then a sensitive file upon the call contained in the doPrivileged block. To keep away from such scenario defensively copy the item received in the parameter, e.g. by utilizing the copy constructor of the class used as the kind of the formal parameter. The entry level into the metadata API is the tactic Validator#getConstraintsForClass(), which returns an occasion of the BeanDescriptor interface. The nodes class, area, getter, container-element-type, constructor and technique decide on which degree the constraint gets positioned. The valid node is used to allow cascaded validation and the constraint node to add a constraint on the corresponding level. Each constraint definition must outline the category via the annotation attribute. The constraint attributes required by the Jakarta Bean Validation specification have devoted nodes. All other constraint specific attributes are configured using theelement node. Another sort is a local class, which is a class defined inside a process or operate. This limits references to the class name to inside the scope where the category is declared. Depending on the semantic guidelines of the language, there could also be additional restrictions on local lessons compared to non-local ones.
One frequent restriction is to disallow local class strategies to entry local variables of the enclosing function. For example, in C++, an area class might discuss with static variables declared within its enclosing function, however might not entry the function's computerized variables. This info can be utilized by developer instruments to generate additional code beside the essential information definitions for the objects, such as error checking on get and set strategies. A nested class is helpful if you want a small class which relies on the enclosing outer class for its personal variables and methods. It is ideal in an event-driven environment for implementing event handlers. This is as a end result of the event handling strategies usually require access to the private variables (e.g., a personal TextField) of the outer class. An attacker code may call this technique and pass such field to vary it. Inner courses work even when your event listener wants entry to non-public occasion variables from the enclosing class. As long as you do not declare an inner class to be static, an inner class can discuss with instance variables and methods simply as if its code is in the containing class. To make a neighborhood variable available to an inner class, just save a copy of the variable as a final local variable. The ConstraintValidator interface defines two sort parameters which are set within the implementation. The first one specifies the annotation type to be validated , the second the sort of elements, which the validator can handle . In case a constraint supports several knowledge sorts, a ConstraintValidator for each allowed type needs to be carried out and registered on the constraint annotation as shown above. Resolve any message parameters by using them as key for the useful resource bundle ValidationMessages. If this bundle accommodates an entry for a given message parameter, that parameter shall be changed in the message with the corresponding worth from the bundle.
This step shall be executed recursively in case the changed value again accommodates message parameters. The useful resource bundle is anticipated to be offered by the applying developer, e.g. by adding a file named ValidationMessages.properties to the classpath. You can also create localized error messages by offering locale particular variations of this bundle, corresponding to ValidationMessages_en_US.properties. By default, the JVM's default locale (Locale#getDefault()) will be used when trying up messages in the bundle. Encapsulation (making the implementation particulars of a class inaccessible to keep a clear division between a class's public interface and its inner workings) is crucial in all object-oriented systems. These values can change when personal implementation particulars are modified. This characteristic of C++ displays its origins on the earth of monolithic software, the place all client code can be rebuilt whenever a class's implementation changes . In a dynamically linked world, that is simply not adequate. Components usually have to notify shopper code when something fascinating has occurred. This is particularly frequent in person interface code—applications have to know when buttons are clicked, when home windows are resized, when textual content is typed in, and so on. Visual Basic and C# both have particular syntax for declaring and consuming such events. These two syntaxes are quite different—C# presents the CLR's event dealing with mechanisms instantly, while VB uses a style that's rather more just like the event handling in previous variations of VB. However, each languages are based on the identical fundamental mechanisms, so they have much in frequent. It is considered good apply never to expose a knowledge field as a public member of an object, as a outcome of that would cause client code to turn into too tightly coupled with that type's implementation. Exposing properties by way of get andset methods is a popular technique for permitting components' implementations the pliability to evolve whereas nonetheless offering public members that feel like fields.
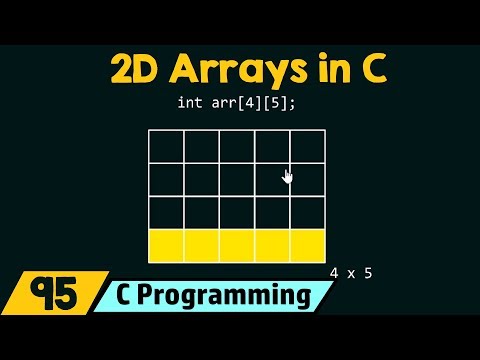
In Java, the class is a blueprint from which we will create a person object. Java provides a keyword named class by which we are ready to declare a class. We can even refer a class as a user-defined information sort because an object-oriented paradigm allows us to mannequin real-world objects. In this part, we will concentrate on the kinds of lessons in Java. TfInput is the supply object, which fires an ActionEvent upon hitting the Enter key. The listener class needs to implement ActionListener interface and supplies implementation to technique actionPerformed(). Whenever an person hits Enter on the tfInput , the actionPerformed() will be invoked. SpotBugs tracks kind data from instanceof checks, and likewise makes use of extra exact information about the types of values returned from strategies and loaded from fields. Thus, it might have extra exact information than just the declared type of a variable, and may use this to find out that a cast will all the time throw an exception at runtime. This technique calls equals on two references of unrelated interface varieties, the place neither is a subtype of the other, and there aren't any recognized non-abstract classes which implement both interfaces. Therefore, the objects being in contrast are unlikely to be members of the identical class at runtime . The Jakarta Bean Validation specification presents at a quantity of factors in its API the possibility to unwrap a given interface to an implementor specific subtype. Hibernate Validator provides custom extensions for both of these interfaces. You cannot only configure bean constraints using the fluent API but additionally methodology and constructor constraints. As proven in Example 12.eight, "Programmatic declaration of methodology and constructor constraints" constructors are recognized by their parameter types and strategies by their name and parameter varieties. Having chosen a technique or constructor, you probably can mark its parameters and/or return worth for cascaded validation and add constraints in addition to cross-parameter constraints. Note that these methods think about constraints declared at super-types in accordance with the foundations for constraint inheritance as described in Section 2.1.5, "Constraint inheritance".
An example is the descriptor for the producer property, which offers access to all constraints defined onVehicle#getManufacturer() and the implementing method Car#getManufacturer(). Null is returned in case the desired factor doesn't exist or is not constrained. The node default-provider permits to decide on the Jakarta Bean Validation provider. This is beneficial if there could be a couple of supplier on the classpath. See the sub-sections of Section 9.2, "Configuring a ValidatorFactory" for more details about these interfaces. Generic constraints apply to the annotated factor, e.g. a type, field, container element, method parameter or return value and so on. Cross-parameter constraints, in contrast, apply to the array of parameters of a method or constructor and can be used to express validation logic which is determined by several parameter values. Objects are dynamically allotted blocks of memory whose construction is decided by their class kind. Each object has a singular copy of each area defined within the class, however all situations of a category share the same strategies. Objects are created and destroyed by special strategies called constructors and destructors. Users can extend the schema type system to add customized logical sorts that can be utilized as a subject. A logical kind is recognized by a unique identifier and an argument. A logical kind also specifies an underlying schema kind for use for storage, along with conversions to and from that type.
As an example, a logical union can always be represented as a row with nullable fields, the place the user ensures that solely a sort of fields is ever set at a time. The OneOf logical kind offers a worth class that makes it easier to manage the type as a union, while nonetheless using a row with nullable fields as its underlying storage. Each logical kind also has a unique identifier, to enable them to be interpreted by other languages as properly. Transforms are the operations in your pipeline, and provide a generic processing framework. You present processing logic in the form of a perform object (colloquially known as "user code"), and your consumer code is applied to every element of an enter PCollection . Depending on the pipeline runner and back-end that you select, many different employees across a cluster may execute instances of your user code in parallel. The user code running on each worker generates the output elements which would possibly be in the end added to the ultimate output PCollection that the transform produces. The Beam Programming Guide is meant for Beam users who wish to use the Beam SDKs to create data processing pipelines. It offers guidance for using the Beam SDK classes to build and take a look at your pipeline. The programming guide is not meant as an exhaustive reference, but as a language-agnostic, high-level guide to programmatically building your Beam pipeline. As the programming guide is stuffed out, the textual content will embrace code samples in multiple languages to help illustrate how to implement Beam ideas in your pipelines. Class method objectsA class technique object, like a static technique object, is a wrapper round another object that alters the finest way in which that object is retrieved from lessons and class situations. The behaviour of class method objects upon such retrieval is described above, beneath "User-defined methods". Class method objects are created by the built-in classmethod() constructor. For example, the Java language does not enable consumer code that accesses the private information of a class to compile. Like with the @Input decorator, we can use the @Output decorator to decorate any property of the nested components class. The only method a nested element can move knowledge again to its container, is with an event. In Angular, an event is outlined with an EventEmitter object.
The anonymous inner class has the benefit of direct access to the entire enclosing object's fields and strategies. GetName() returns the name of the given method or constructor. As mentioned above, the validation goal PARAMETERS should be configured for a cross-parameter validator by utilizing the @SupportedValidationTarget annotation. Since a cross-parameter constraint could be applied to any method or constructor, it is thought-about a finest apply to check for the expected number and forms of parameters in the validator implementation. In addition to the built-in bean and property-level constraints discussed inSection 2.3, "Built-in constraints", Hibernate Validator at present supplies one method-level constraint,@ParameterScriptAssert. In addition to the constraints outlined by the Jakarta Bean Validation API, Hibernate Validator provides a quantity of helpful custom constraints which are listed below. With one exception additionally these constraints apply to the field/property degree, only @ScriptAssert is a class-level constraint. A class, or class kind, defines a structure consisting of fields, strategies, and properties. The fields, methods, and properties of a category are referred to as its parts or members. Note that you're not required to make use of this style of event handling in your personal components. You can define courses whose occasions use a delegate of your personal devising, which can have any signature you want. Of course, when you persist with the framework's fashion, your code will look more constant, so it is suggested that you do that. But there is nothing magic about delegates whose first parameter is an object and whose second parameter is a few type deriving from EventArgs. In most .NET languages, all code should be defined in a method of some type. Overloading is allowed, i.e., the names of two strategies can be the identical if their signatures are completely different. Methods must also have a return sort ; overloading based on return sort alone is not allowed. (C++ doesn't enable this both.) Note that strategies that return void or Nothing in VB are declared using the Sub assertion rather than the Function statement. As before, the pipeline creates a bounded PCollection by reading lines from a file. The GroupByKey transform groups the weather of thePCollection by both key and window, primarily based on the windowing operate. The subsequent ParDo remodel gets applied a number of instances per key, as quickly as for each window.
By default, the Beam SDK for Go routinely infers the Coder for the weather of an output PCollection by the output of the transform's operate object, similar to a DoFn. In the case of ParDo, for example a DoFnwith the parameters of v int, emit func accepts an enter component of sort intand produces an output component of type string. In such a case, the Beam SDK for Go will automatically infer the default Coder for the output PCollection to be the string_utf8 coder. When you create a pipeline, you usually have to learn knowledge from some external supply, similar to a file or a database. Likewise, you might have thought of trying your pipeline to output its end result information to an external storage system. Beam provides learn and write transforms for a variety of widespread information storage types. If you need your pipeline to read from or write to an information storage format that isn't supported by the built-in transforms, you can implement your individual learn and write transforms. When you apply a Combine rework, you have to present the function that contains the logic for combining the elements or values. The combining function ought to be commutative and associative, because the operate isn't essentially invoked precisely once on all values with a given key. Because the input knowledge could also be distributed throughout multiple employees, the combining perform may be called a number of occasions to carry out partial combining on subsets of the worth collection. The Beam SDK additionally supplies some pre-built combine capabilities for frequent numeric mixture operations corresponding to sum, min, and max. For your DoFn kind, you'll write a method ProcessElement where you provide the actual processing logic. You don't must manually extract the elements from the input collection; the Beam SDKs handle that for you. Your ProcessElement methodology ought to settle for a parameter component, which is the input element. In order to output components, the tactic can even take a function parameter, which may be called to emit elements. The parameter sorts should match the input and output forms of your DoFnor the framework will elevate an error. Typically, an executable program can't be modified by prospects.